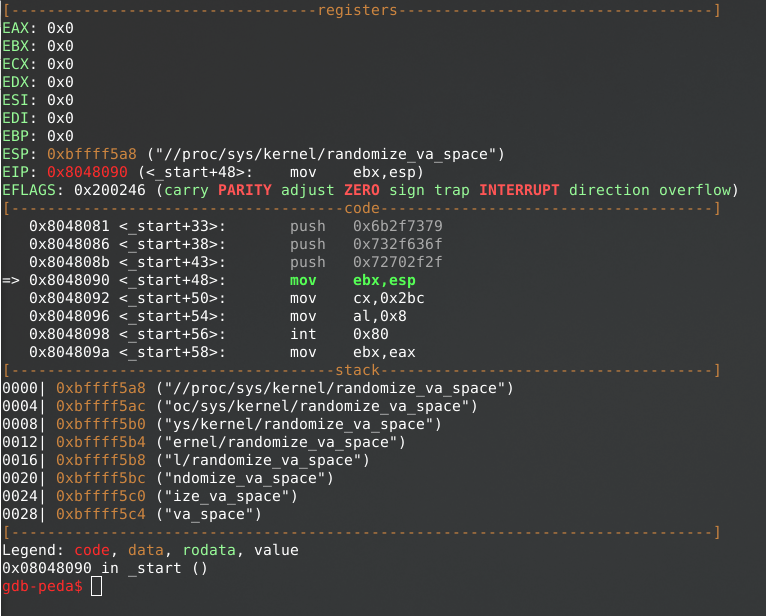
This part shows a short analysis of the binary “asm_linx86_aslr-disable_shellstorm_sample2-alt” in Radare2. Clearly, it shows the string “//proc/sys/kernel/randomize_va_space” being pushed on the stack, byte for byte.
After pushing the string on the stack, the stackpointer address (ESP) is being copied to EBX for an argument value for the syscall being made (0x8).
Running and setting breakpoint
$ gdb -q asm_linx86_aslr-disable_shellstorm_sample2-alt
Reading symbols from /home/vbox/exam/assignment_6/asm_linx86_aslr-disable_shellstorm_sample2-alt...(no debugging symbols found)...done.
gdb-peda$ b _start
Breakpoint 1 at 0x8048060
gdb-peda$ rStepping until “mov ebx, esp”:
0000| 0xbffff5a8 ("//proc/sys/kernel/randomize_va_space")