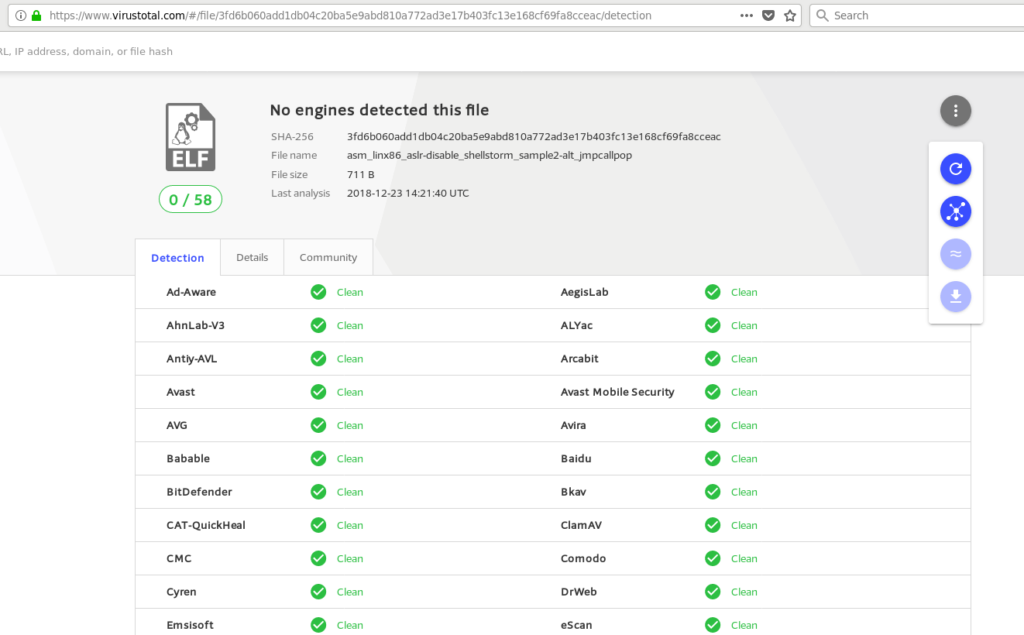
Let’s upload the compiled binary to check if any anti-virus gets triggered:
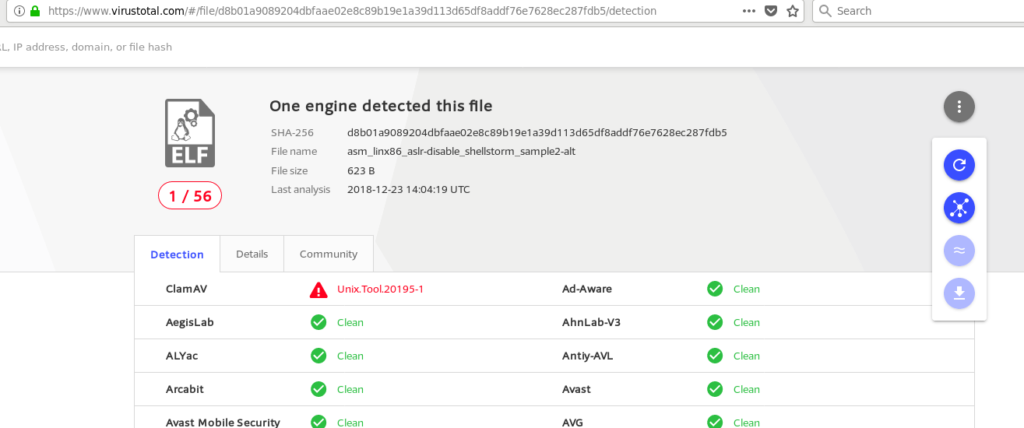
Just one engine detected something malicious. Again, this might be caused due to pushing certain known static strings on the stack.
Making modifications using JMP/CALL/POP
In an attempt to mitigate this, we’ll be using the JMP/CALL/POP technique to pop certain strings in registers by function return calls.
I’ve had to manually add a clear registry instruction for the exit function, due to increment instruction which expected the EAX registry to be zero.
; sys_exit
xor eax, eax ; Clear register
inc eax ; Previous value after syscall was 0, increment for 1
int 0x80 ; syscall exitCompiling and uploading again:
$ ../compile_asm.sh asm_linx86_aslr-disable_shellstorm_sample2-alt_jmpcallpop
[+] Assembling with Nasm ...
[+] Linking ...
[+] Done! After uploading the file, no engines complained.